

The WIse SECurity
.english
 The WIse SECurity
| .italian .english |
|
News
|
Security Thoughts[ Back ] Wednesday, April 21, 2010, 16:16 Facebook application hole. A neverending story? It was April 11th @ 9:00 AM,some days before my Campusparty talk, and I decided to have a quick look at Facebook apps howto implementations.
Which, if user has already subscribed to the application, then it redirects to :
The url where the user is redirected can be set in the 'next' parameter (implied in moreParameters). Now I had to better understand what I can do and went to my favourite FaceBook hacker-superhero The Harmony Guy. Found this: It seems he already found something...and very big! :( Even if I don't know a thing about FBK, I was sooo near! The good^N^N^N^NBad thing is that it took me a few hours to study the environment and think about that. That's the explaination (from harmony guy link):
Now there's something I don't understand, and that's because I'm not a Facebook hacker and because the description is not technical. They say it's fixed but if I try this request: http://www.facebook.com/tos.php?api_key=80c6ec6628efd9a465dd223190a65bbc&connect_display=popup&v=1.0&next=../wisectest/&v=1.0&&return_session=true&session_key_only=true&canvas using farmville api_key with next parameter set to my test application home page on apps.facebook.com, I get a redirect to: http://apps.facebook.com/wisectest/?session={"session_key":"2.XXXXXXXXZzHYZaBMEA__.3600.XXXX-XXXXX","uid":XXXXXX,"expires":1271016000,"secret":"XXXXXX","base_domain":"farmville.com","sig":"XXXXX"} After that the victim seems to be also added my fake test app transparently... 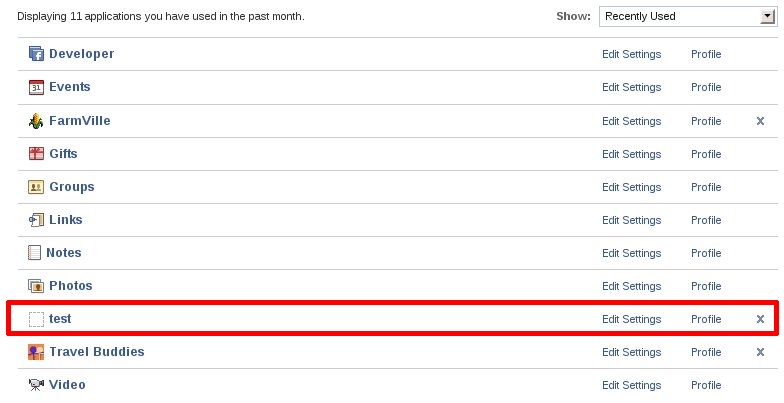 Maybe they fixed on login.php but missed some page?...:o As usual the infamous question I asked myself a lot of times when a vuln is fixed but the technique has not been understood. How come that after the "theharmonyguy" post no one @facebook got a deep analysis? Maybe complexity is a bad dwarf when dealing with security, but what about applying Secure-SLDC, I mean, really. Just for sake of user privacy protection, I'd suggest to use different Browsers or Firefox Plugins.
Nota Bene: I also found some site publishing Xss on facebook applications by simply searching on google...and they still work! Hey Mr. Facebook would you care doing a Google search? A hint: "facebook applications security bugs" on bigG. Comments: theharmonyguy, Wednesday, April 21, 2010, 17:07 Wow great find - they fixed the "next" parameter for an absolute URI, but not the relative URI you put in. I just confirmed the bug and will report it to my contact at Facebook, giving you full credit of course. Stefano, Wednesday, April 21, 2010, 17:21 theharmonyguy, theharmonyguy, Wednesday, April 21, 2010, 17:59 True, though it would need to be XSS in an app page that does not require you to be authenticated for *that* app also. Executing the API requests immediately would also ensure the session data doesn't expire before you use it. Stefano, Wednesday, April 21, 2010, 18:04 Now is more clear Comments are disabled
Admin login | This weblog is from www.mylittlehomepage.net Wisec is brought to you by...Wisec is written and mantained by Stefano Di Paola. Wisec uses open standards, including XHTML, CSS2, and XML-RPC. |
All Rights Reserved 2004
All hosted messages and metadata are owned by their respective authors.